A Primer on Zero Trust: Prevention
By Paramesh Vaidyanathan, Skytop Contributor / August 22nd, 2022
Paramesh Vaidyanathan is a software technologist with over three decades of experience. Based out of the Seattle area, Paramesh spent 23 years building software and leading teams at Microsoft Corporation. His experience spans platform and infrastructure software (Microsoft Windows family of products), and developer tools (Microsoft Visual Studio). With an initial focus on local area networking performance and quality, Paramesh went on to lead large engineering teams there. His stint included a five year stint as one of the key leaders of Microsoft’s India Development Center in Hyderabad, India. Since “retiring” from Microsoft in 2012, Paramesh has spent his time, efforts and money working with, advising, and investing in software startups in the fields of Healthcare, Education, and Cybersecurity. He consults through his company, Yenodu LLC, that he co-founded with his wife in 2012. His current focus is on helping companies large and small, particularly in Healthcare, become more Cybersecurity aware and ready.
Paramesh has a Master’s Degree in Electrical (Computer) Engineering from Virginia Tech, and a Bachelor’s Degree in Electrical and Electronics Engineering from Anna University, Chennai, India. In his spare time, Paramesh dabbles in gardening, reading and playing bridge.
Perimeter-Based Network Security
In enterprises, perimeter-based network security mechanisms have been shown to be insufficient. Cyber attackers, until recently, have focused on specific computers, networks, or data storage. Traditionally, enterprises have operated within tight firewalls and gateway devices, with data stored on premises. However, that model has changed significantly. More employees are working remotely, and on personal and sometimes unsecured devices. Enterprises are working with more third parties whose networks have varying levels of protection. Further, there are more and more devices being added to the enterprise network. All of this expands the attack surface available to cyber criminals to target. Consider the following statistics in the enterprise:
Number of 5G mobile connections (excluding IoT) by 2025 – 1.8 billion
Number of cellular IoT connections by 2025 – 3.7 billion
Number of network-connected physical assets by 2023 —29.3 billion
White-collar employees working from home – 67% (41% all the time, 26% part of the time)
Business-impacting cyberattacks targeted remote employees – 67%
Recent cyberattacks due to a third-party software compromise – 65%
Increased risk due to an enterprise’s expanded software supply chain – 61%
80+% of all attacks involve credentials use or misuse in the network
Cyber Attackers and Weak Links
Cyber attackers continue to look for weak links – devices with poor security, employees accidentally kicking on malicious links, piggybacking on weak partner networks, etc., to breach the perimeter defenses of the enterprise. And once they are in, they can freely move within the enterprise laterally, unnoticed, and unhindered for months. Applications, users, and devices need fast and secure access to data. Zero Trust is a strategic framework that offers adaptive and continuous protection for users, data and assets, and the ability to manage threats proactively. Enterprises can also gain insights so that security policies can be consistently applied, and threats can be responded to quickly and effectively.
The Zero Trust Concept
Zero Trust (ZT) is a strategy aimed at preventing unauthorized access to data and services while enforcing access control to those resources to be as granular as possible. ZT is premised on a “do not trust, but verify” principle, where an enterprise makes no implicit trust on any user or request while continually analyzing and evaluating the risks to its assets and business functions. Access to resources (such as data and compute resources and applications/services) are strictly restricted to only those entities that need access. Every access request is authenticated and authorized, and only the minimal privileges (e.g. read, write, delete) are granted only to the entities that need to perform the actions.
Zero Trust Architecture (ZTA) is the comprehensive plan employed by an enterprise. Built on zero trust encompassing resource and data security, ZTA includes identity, credentials, access management, operations, endpoints, hosting environments, and the interconnecting infrastructure.
Assumptions
In order that enterprises may have the most comprehensive security protection, a deployment of Zero Trust makes the following assumptions:
The enterprise network has already been breached.
Never inherently trust any resource.
Verify always.
Not all enterprise devices or resources are enterprise owned. With employees working from home, enterprises should assume that devices and remote networks used to access the corporate network are not secure.
Third-party networks are insecure. Not all third-party, remote partner networks have the same level of security as the enterprise networks.
Tenets of a Zero Trust Architecture
The fundamental principles of a Zero Trust system that is architected “to trust nothing and verify everything” are:
All data sources and computing services are considered resources – regardless of the device or service, its location, its role or its ownership, any device or service that accesses the enterprise is deemed to be a resource.
All communication is secured regardless of network location – a device is not considered trustworthy just because it is operated inside an enterprise network. Each asset used to access any enterprise resource must meet the same security standards regardless of where the access request originated.
Access to individual enterprise resources is granted on a per-session basis – each access request is validated separately, even if a requester was previously granted access. The access granted is with the absolute minimum privileges required to complete a task. A grant of access to one resource does not guarantee automatic access to another resource.
Access to resources is determined by dynamic policy that takes into account behavioral and environmental attributes – An organization sets up a policy for access to its resources. A policy is the set of access rules that an organization assigns to a user, a resource, or an application. This policy definition includes all resources in the enterprise, requesting clients (user or service accounts), what access to resources those clients need, and specifically when they are needed. These definitions can also include device states such as software versions installed, network location, time/date of request, previously observed behavior, and credentials. The dynamic policies can also specify behavioral and environmental attributes – e.g., gathering of device or subject analytics, network location, time and deviations from expected or observed usage patterns.
The enterprise monitors and measures the integrity and security posture of all owned and associated assets – The enterprise employs a continuous diagnostics and mitigation (CDM) process to monitor the state of devices and applications. This allows the enterprise to quickly react to any attacks on these devices or applications.
All resource authentication and authorization are dynamic and strictly enforced before access is allowed – Using dynamic policies and backed by strong authentication techniques like multi-factor authentication (MFA), enterprises should continually monitor, reauthenticate and reauthorize whenever there is a user transaction – e.g., time-based, when a new resource is requested, when a resource is a about to be modified.
The enterprise collects as much information as possible about the current state of assets, network infrastructure and communications and uses it to improve its security posture – This not only helps keep the enterprise secure, but it also allows for the dynamic policies to be adjusted to become more agile and efficient.
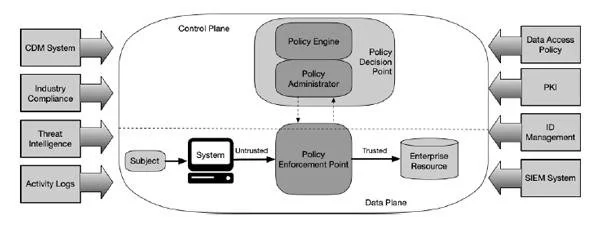
Core Components of a Zero Trust Architecture
Source: https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-207.pdf
A Zero Trust architecture is implemented with a goal to protect against unauthorized access by any subject (user, application, service or device) to any resource (data, services, applications, IoT, printers, etc.). When any authorized subject needs to access a resource, it is granted only the least privileges required to perform the action. This is done by implementing strict access policies (Policy Decision Point, or PDP) and enforcing them appropriately (Policy Enforcement Point, or PEP). While focused on authentication, authorization, and a strictly restricted “trust zone”, a ZT system is implemented to avoid performance, availability, and usability issues.
The PDP and PEP are kept as close to the accessed resources as possible so that all accesses can be tightly monitored, authorized, and managed. The PDP and PEP together form the core logical components of a Zero Trust Architecture.
The Policy Decision Point (PDP) is further made up of two subcomponents – the Policy Engine (PE) that uses enterprises policies and input from external data sources to ultimately grant or deny access to a resource request; and a Policy Administrator (PA) that executes access decisions, made by the PE, between a requesting subject and a requested resource. The PE and PA communicate via an internal “Control Plane” once the PE has decided to grant or deny access.
The Policy Enforcement Point (PEP) enables, manages, monitors, and terminates connections between a subject and an enterprise resource. The PEP communicates with the PA to forward requests and/or receive policy updates from the PA. To enter the “trust zone” that hosts the enterprise resources, any subject must go through the PEP. All communications between the PEP and external data sources happen via a “Data Plane.”
Additional Components of a Zero Trust Architecture
Source: https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-207.pdf
The Policy Engine uses several sources of data, both inside and outside the enterprise, in addition to the policies implemented by the enterprise, to grant or deny access. The data sources form the additional components of the ZTA. Depending on the implementation of the ZTA, these components could include:
Continuous diagnostics and mitigation (CDM) system – provides data on the state, configurations, and versions of software on all enterprise assets and non-enterprise-owned devices that make access requests.
Industry compliance system – ensures that all regulatory and enterprise policy requirements are complied with.
Threat intelligence feed(s) – gathers and provides threat and attack information from all sources, internal and external.
Network and system activity logs – in real-time gathers and makes available comprehensive information on the security status of all enterprise assets.
Data access policies – the fundamental set of rules, both encoded and dynamically generated, based on the needs of the enterprise, that the engines use to authorize or deny access requests.
Enterprise public key infrastructure (PKI) – system used to generate certificates for use by all enterprise entities (resources and subjects).
ID management system – basic system used to create and manage accounts for all users and assets in the enterprise.
Security information and event management (SIEM) – the system used to gather security-centric information about the enterprise assets for analysis, adjustment of policies and identification/protection against possible cyber-attacks.
Network Requirements for the Enterprise in a Zero Trust Architecture
With the principles, assumptions and components of a Zero Trust enterprise defined, it is important to specify the basic network requirements to successfully implement a ZTA. While some of them may be obvious, they are all worth explicitly stating:
Basic network connectivity – each asset in the enterprise must have, available to it, basic network connectivity including routing and infrastructure, at all times.
All assets owned or managed by the enterprise, along with their security status, can be identified uniquely, and at all times.
All enterprise network traffic packets can be observed all the time.
Each access to any enterprise resource must go via a PEP (Policy Enforcement Point). The PEP is the last gateway to a resource.
Since all requests must be routed through a PEP, it follows that all enterprise assets must be able to access the PEP.
The Control Plane is exclusively used by the PA/PE and PEP to communicate on policy matters. All communication between the PEP and other input sources happen on a Data Plane. It can then be concluded that the Control Plane and the Data Plane are separate entities.
The Policy Enforcement Point (PEP) is the only entity that can access the Policy Administrator component (PA).
Remote enterprise assets should not have to traverse the entire network to access an enterprise resource.
The Policy Engine, Administrator and Enforcement Points should be scalable to meet any increase in workloads without perceptible performance or usability issues.
Not all enterprise subjects should be able to access all PEPs.
Protection & Mitigation Strategies
Any enterprise strategy must be founded on a specific mission. In this case, the goals are to protect the enterprise from cyber-attacks, identify and mitigate an attack as quickly as possible, and proactively look for signs that might indicate a future attack. Specifically, the Zero Trust system should be able to:
Identify the critical resources (Data/Assets/Applications/Services) and secure them.
Protect the critical resources, and strongly secure all paths to access them.
Determine who/what needs access to the resources, then create access control policies based on:
Why does an access need to be accessed? Who needs to access it? Where from?
Create and apply security policies consistently across all environments (LAN, WAN, endpoint, perimeter, mobile, etc.).
Monitor and log all traffic in detail across all layers, endpoints, and the network to enable analytics that can detect spurious activity.
The following tactics form the basic protection and mitigation steps required to secure the enterprise:
Keep all Software up-to-date => Update, upgrade all software, ideally on an automated basis.
Enforce Signed Software Execution Policies => use modern operating systems that enforce signed software execution policies for scripts, executables, device drivers, and system firmware.
Leverage Modern Hardware Security Features => Use hardware security features like Unified Extensible Firmware Interface (UEFI) Secure Boot, Trusted Platform Module (TPM), and hardware virtualization.
Segment Networks, Use Application-Aware Defenses => Segment critical networks and services. Employ application-aware network defenses to block spurious traffic and restrict content to whatever is set by policies.
Deploy Multi-Factor Authentication => Prioritize protection for accounts with elevated privileges, remote access, and/or used on high value assets. Use “what you have” (physical) token-based authentication systems to supplement “what you know” (knowledge) such as passwords and PINs. Aggressively move away from single factor authentication (e.g. just passwords).
Defend Privileges and Accounts => Privileged Access Management (PAM) – automate credential management and fine-grained access control. Use tiered administrative access, protect higher-tiered accounts more tightly.
Actively Manage Systems and Configurations => Restrict enterprise network to run only known hardware/software as a baseline. With a known starting point, control of the operational environment is established. Then, actively manage devices, applications, operating systems, and security configurations.
Be Ready with a System Recovery Plan => a recovery plan must protect critical data, configurations, and logs to ensure continuity of operations in the event of unexpected attacks. Full, encrypted backups stored offsite, and ideally offline, will support complete and quick recovery.
Proactively look non-stop for Network Intrusions => Detect, contain, and remove any malicious presence within the network. Enterprises should assume that an intruder has already breached the network and resides within. Using dedicated teams seek out, contain, and remove threat actors within the network. Passive detection mechanisms, such as logs, Security Information and Event Management (SIEM) products, Endpoint Detection and Response (EDR) solutions, and other data analytic capabilities are invaluable tools to find malicious or anomalous behaviors. In addition, active pursuits (“hunt” operations and penetration testing) should be used to address any discovered breaches in security.
Threat Reputation Services (TRS) => Leverage multi-sourced threat reputation services for files, DNS, URLs, IPs, and email addresses. Reputation services assist in the detection and prevention of malicious events and allow for rapid global responses to threats, a reduction of exposure from known threats, and provide access to a much larger threat analysis and tipping capability than an organization can provide on its own. Emerging threats, whether targeted or global campaigns, occur faster than most organizations can handle, resulting in poor coverage of new threats.
Benefits of Moving to a Zero Trust Model
A 2021 study shows the tangible financial benefits of moving to a Zero Trust model in the enterprise. Businesses that choose to adopt the model see a quick return on investment too. Organizations across all stages of deployment reported lower breach costs than those that hadn’t deployed zero trust at all.
Organizations without Zero Trust: $5.04M per breach
Organizations with full Zero Trust: $3.28M per breach
Organizations in early stages of Zero Trust: $4.38M per breach
Organizations in mid stages of Zero Trust: $3.71M per breach
Deploying a higher standard of encryption for data storage and transfer tends to reduce the cost incurred in a security breach, and this is one of the tactics used in Zero Trust.
Using lower standard encryption: $4.87M per breach
Using higher standard (e.g. 256-bit AES Encryption): $3.62M per breach
It is worth recalling that another tenet of Zero Trust is to be always aware of the users and devices on the network, and to monitor their security state. Using Artificial Intelligence, Machine Learning and security automation for this purpose resulted in savings to organizations over those that did not deploy them.
Organizations without AI/ML/automation: 324 days to detect and contain breach.
Organizations with AI/ML/automation: 247 days to detect and contain breach.
A higher breach cycle means lost revenue and more dissatisfied customers. This saving
The above examples clearly demonstrate that even a partial implementation of Zero Trust can result in increased security and significant cost benefits for the enterprise.
A different study on the benefits of implementing a specific Zero Trust solutions showcase more benefits, financial and otherwise, of using Zero Trust in an enterprise:
A three-year 92 percent return on investment (ROI) with a payback period of fewer than six months.
A 50% lower chance of a data breach.
Many efficiency gains of 50+% across security processes.
43% of the companies that partook in the first study reported no plans to adopt a Zero Trust solution. With more frequent cyber-attacks, the lack of a Zero Trust solution would be devastating to the top line and bottom line of organizations. On the other hand, full implementations, although they would take time, could result in significant savings both financially and from the perspective of reputation.